Your Guide to the Perfect Defense: Unlocking the Secrets of The Right Defense For Your Program Volume

In the realm of software development, safeguarding your program against malicious attacks is paramount. Every line of code, every component, and every vulnerability presents a potential entry point for adversaries seeking to exploit your system. To effectively mitigate these risks, a robust defense mechanism is essential, and "The Right Defense For Your Program Volume" serves as your ultimate guide to building an impenetrable fortress against cyber threats.
Delving into the Depths of Security Concepts
This comprehensive volume delves into the intricacies of software security, providing a thorough understanding of the fundamental concepts and techniques employed to protect your programs. You'll explore:
4 out of 5
| Language | : | English |
| File size | : | 3537 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 79 pages |
| Lending | : | Enabled |
- The anatomy of attacks: Learn about the various types of attacks, their motivations, and the vulnerabilities they exploit.
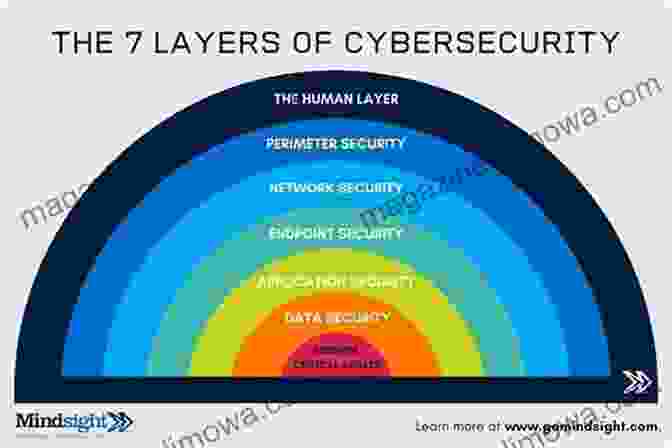
- Defense-in-depth: Discover the multi-layered approach to security, where multiple defenses work together to minimize the impact of attacks.
- Common security flaws: Identify and address the most prevalent security vulnerabilities, such as buffer overflows, SQL injections, and cross-site scripting.
Practical Implementation: Fortifying Your Codebase
Beyond theoretical knowledge, "The Right Defense For Your Program Volume" provides practical guidance on implementing effective security measures. You'll delve into:
- Secure coding practices: Learn how to write secure code from the ground up, minimizing the of vulnerabilities.
- Security testing techniques: Discover the various testing methods used to identify and remediate security flaws before they can be exploited.
- Best practices for secure software development: Explore industry-standard practices and frameworks to ensure the security of your software throughout its lifecycle.
Case Studies and Real-World Examples
Reinforcing the theoretical concepts, "The Right Defense For Your Program Volume" presents real-world case studies and examples. You'll learn from the experiences of others, examining successful and failed security implementations and gaining invaluable insights into the practical application of security principles.
Advanced Defense Strategies for Complex Systems
As software systems grow increasingly complex, traditional security measures may prove insufficient. This volume delves into advanced defense strategies designed to protect distributed systems, cloud-based applications, and mobile platforms. You'll explore:
- Network security: Understand the principles of network security, including firewalls, intrusion detection systems, and virtual private networks.
- Cloud security: Discover the unique challenges and best practices for securing cloud-based infrastructure and applications.
- Mobile security: Learn about the specific security considerations and vulnerabilities associated with mobile devices and applications.
and Continuing the Journey
"The Right Defense For Your Program Volume" concludes by emphasizing the importance of continuous vigilance in software security. As technology evolves and new threats emerge, it's essential to stay abreast of the latest security trends and best practices.
Additional Resources
- Website for The Right Defense For Your Program Volume
- Author's blog on software security
- Online community for software security professionals
Image Alt Attributes
4 out of 5
| Language | : | English |
| File size | : | 3537 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 79 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Jim Brault
Jim Brault John Mcdermott
John Mcdermott John H Cunningham
John H Cunningham John Grabowski
John Grabowski Joe Bruno
Joe Bruno Stephanie Hammond
Stephanie Hammond Sally Gardner
Sally Gardner Michael Lenehan
Michael Lenehan Joe Bruce
Joe Bruce Jim Loomis
Jim Loomis John C Hall
John C Hall Karri Thompson
Karri Thompson John Laskowski
John Laskowski John Waterbury
John Waterbury John Hope
John Hope John Lucas
John Lucas Joe Gisondi
Joe Gisondi Susan Sessions Rugh
Susan Sessions Rugh John Milton
John Milton Rodney Paul
Rodney Paul
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 William WordsworthUncover the Hidden Treasures of the Disney Cruise Line: An Exclusive Guide
William WordsworthUncover the Hidden Treasures of the Disney Cruise Line: An Exclusive Guide
 Brett SimmonsKids Picture About Starfish With Photos And Fun Facts: An Enchanting Journey...
Brett SimmonsKids Picture About Starfish With Photos And Fun Facts: An Enchanting Journey... Dean ButlerFollow ·13.3k
Dean ButlerFollow ·13.3k Ralph EllisonFollow ·16.9k
Ralph EllisonFollow ·16.9k Jake CarterFollow ·19.7k
Jake CarterFollow ·19.7k Bradley DixonFollow ·9k
Bradley DixonFollow ·9k Harvey HughesFollow ·17.8k
Harvey HughesFollow ·17.8k Hayden MitchellFollow ·7.3k
Hayden MitchellFollow ·7.3k Marc FosterFollow ·2.8k
Marc FosterFollow ·2.8k Jeffrey CoxFollow ·15.9k
Jeffrey CoxFollow ·15.9k

 Joshua Reed
Joshua ReedTake Your Marketing Business Into The Next Level
Are you ready to...

 Aaron Brooks
Aaron BrooksFrom Fourier to Cauchy-Riemann: Geometry Cornerstones
From Fourier to Cauchy-Riemann: Geometry...

 Orson Scott Card
Orson Scott CardUnveiling the Art of Mitigation Banking: A Comprehensive...
In the intricate dance between...

 Victor Hugo
Victor HugoUnleash Your Creativity: A Journey Through the Enchanting...
Prepare to be captivated as we...

 Duncan Cox
Duncan CoxLoad of Bull: An Englishman's Adventures in Madrid
By Simon Bunce ...
4 out of 5
| Language | : | English |
| File size | : | 3537 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 79 pages |
| Lending | : | Enabled |